As part of a series on using HTTPS Everywhere we are migrating a website from HTTP to HTTPS. Previously we configured our web server with an SSL certificate, and we are now ready to configure the SSL engine on our server.
For this article I will mention the best practices for configuring both your Apache and IIS web server. For the IIS configuration I will be using the free IIS Crypto tool by Nartac Software.
FWIW, I am not a security expert. So, I am following the best practices as prescribed by Mozilla on their server side TLS article.
Apache Web Server
For the apache configuration I will generally copy/paste the recommended configuration from Mozilla. Here is what I did:
- Paste the recommended configuration for Apache
- Make any necessary updates based on my Apache version
- Paste the intermediate compatibility ciphers preference for the “SSLCipherSuite” property
These modifications are made to the httpd-ssl.conf file, which is located for me at: /etc/apache2/extra/httpd-ssl.conf.
#General setup for the virtual host
DocumentRoot "/www/local.example.com/www"
ServerName local.example.com
ErrorLog "/private/var/log/apache2/local.example.com-error_log"
CustomLog "/private/var/log/apache2/local.example.com-access_log" common
#SSL Engine Switch:
SSLEngine on
#Server Certificate:
SSLCertificateFile "/private/etc/apache2/ssl/local.example.com.crt"
#Server Private Key:
SSLCertificateKeyFile "/private/etc/apache2/ssl/local.example.com.key"
#SSL Engine Options:
<FilesMatch "\.(cgi|shtml|phtml|php)$">
SSLOptions +StdEnvVars
<Directory "/Library/WebServer/CGI-Executables">
SSLOptions +StdEnvVars
# Intermediate configuration, tweak to your needs
SSLProtocol all -SSLv2 -SSLv3
SSLCipherSuite "ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!3DES:!MD5:!PSK"
SSLHonorCipherOrder on
SSLCompression off
# On Apache 2.4+, SSLStaplingCache must be set *outside* of the VirtualHost
SSLStaplingCache shmcb:/var/run/ocsp(128000)
The SSL configuration above does the following.
- The first property named
SSLProtocoltells OpenSSL to use all protocols except for the outdated SSL version 2.0 and 3.0 protocols. - The second property named
SSLCipherSuiteis a listing of the preferred ciphers to use. This is the string that I obtained from the Mozilla page, and note that it is surrounded by double-quotes. The order of the ciphers will matter when we set the next property. - The third property named
SSLHonorCipherOrdersays that the order of the ciphers listed is the preferred order to use when establishing a secure connection. We simply set this to on.
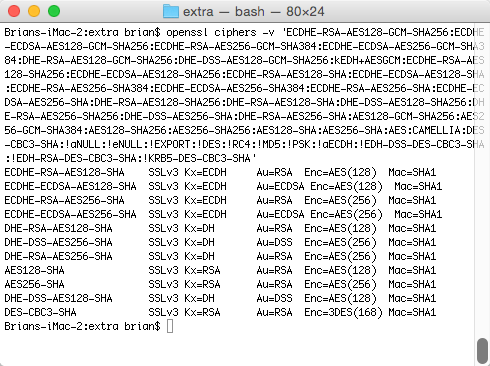
As a side note, you can validate that your openssl version supports the ciphers. Just copy the list of ciphers into the following command:
$ openssl ciphers -v 'ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA'The result of running this command indicates that all ciphers are supported.
As always, we want to test our Apache configuration and restart the server. Assuming everything is OK, we should be able to pull up our HTTPS site in a modern browser.
IIS Crypto
Setting up the IIS cryptography is simplified greatly by using a free tool from Nartac Software called IIS Cryto. Download IIS Crypto
The download is just a .exe file. Copy this to the desktop and launch it. I will simply select the Best Practices option and click Apply. These options will disable the old protocols (SSL v 2.0 and 3.0) and will set the recommended cipher suites.
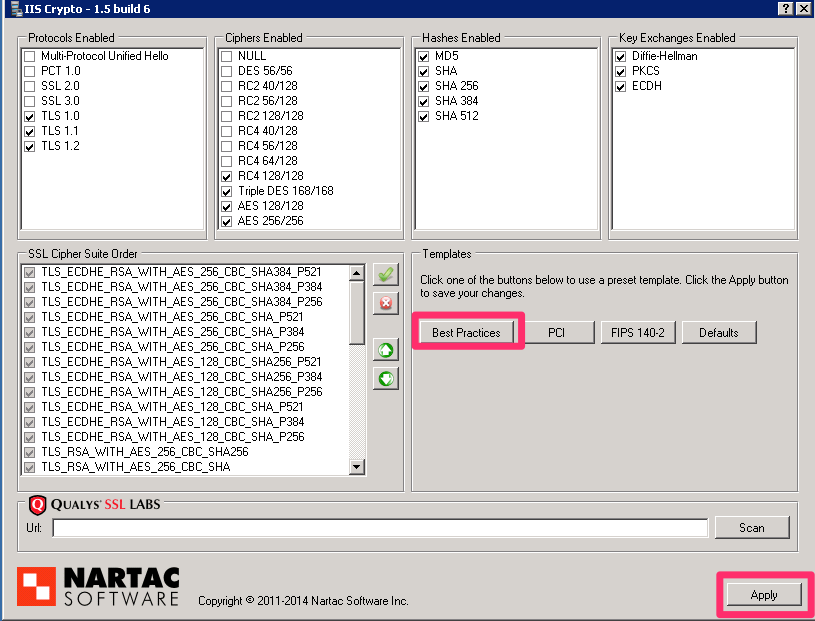
After applying the new settings be sure to restart the Windows server.
Testing SSL
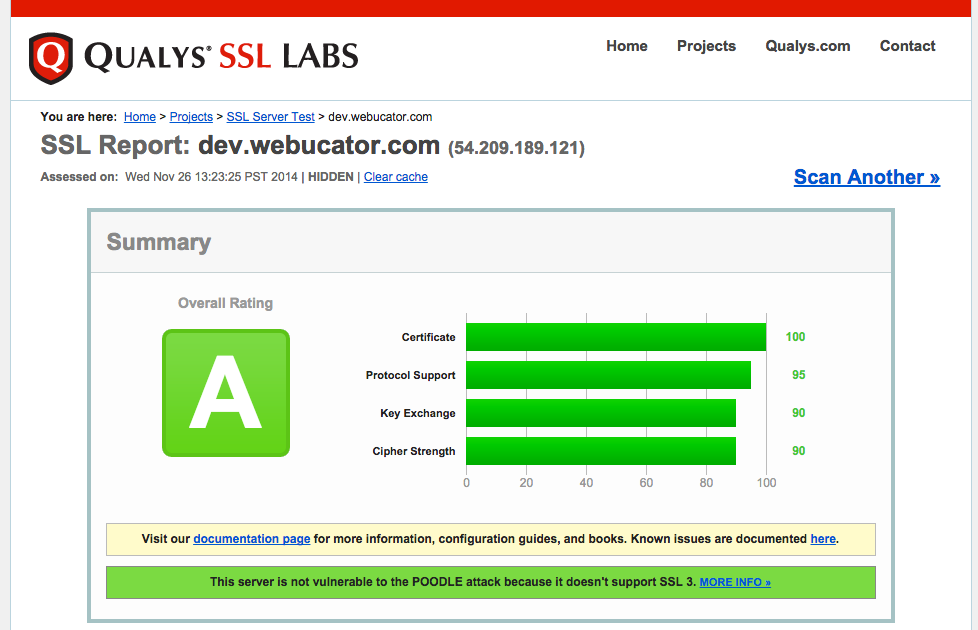
The last step is to test our SSL configuration. There are three popular, and free, tools that will help you. I prefer to use the Qualys tool.
- Qualys SSL Labs
- SSLyze (Python)
- CryptoNark (Perl)
Here is a screen shot of my score from the Qualys SSL Labs website.